Information technology and medical technology personnel’s perception regarding segmentation of medical devices: A focus group study
| Full article title | Information technology and medical technology personnel’s perception regarding segmentation of medical devices: A focus group study |
|---|---|
| Journal | Healthcare |
| Author(s) | Johansson, David; Jönsson, Patrik; Ivarsson, Bodil; Christiansson, Maria |
| Author affiliation(s) | Edith Cowan University, Embry-Riddle Aeronautical University |
| Primary contact | Email: david dot a dot johansson at skane dot se |
| Year published | 2020 |
| Volume and issue | 8(1) |
| Page(s) | 23 |
| DOI | 10.3390/healthcare8010023 |
| ISSN | 2227-9032 |
| Distribution license | Creative Commons Attribution 4.0 International |
| Website | https://www.mdpi.com/2227-9032/8/1/23 |
| Download | https://www.mdpi.com/2227-9032/8/1/23/pdf (PDF) |
Abstract
Objective: Segmentation is one way of improving data protection. The aim of this study was to investigate information technology (IT) and medical technology (MT) personnel’s perception in relation to ongoing segmentation of medical devices and IT infrastructure in the healthcare sector.
Methods: Focus group interviews with nine IT and nine MT personnel in a county council in southern Sweden were conducted. The interviews focused on two areas: positive expectations and misgivings. Digital recordings were transcribed verbatim and analyzed using qualitative content analysis.
Results: Responses related to two main areas: information security and implementation of segmentation. Informants stated that network segmentation would increase the overall level of cybersecurity for medical devices, addressing both insider and outsider threats. However, it would also increase the need for administration and the need for knowledge of the communication patterns of medical devices from the manufacturer’s perspective.
Conclusion: IT and MT personnel in a county council in southern Sweden believed that segmentation would increase cybersecurity but also increase administration and resource needs, which are important opinions to take into consideration. The present study can be used as a model for others to increase awareness of opinions of healthcare organizations.
Keywords: cybersecurity, healthcare technology, patient safety, staff attitudes
Introduction
Medical technology (MT) devices—as defined by the European Union's directive on medical devices[1] and information technology (IT) and device developers—serve an increasingly central role in clinical practice, improving patient health, safety, and quality of life. And the number of such medical devices that are connected to a network continues to grow.[2][3][4]
Networked medical devices can also cause substantial harm since they have not historically been designed with a focus on cybersecurity.[5] Errors that underlie device-related injuries are often categorized into three types: manufacturer-related errors, use or design errors, and user errors.[6] It has been said that the weakest link in the process is the user, who must understand how to configure and use medical technology products correctly to achieve a high level of security in computing infrastructure.[7][8]
Cybersecurity is today one of the most important security-related challenges for all countries, but its visibility and awareness are still limited to the public, although almost everyone has heard something about it.[9] There is a substantial security risk posed by outsiders identifying potential interactions between the interconnected elements in hospital systems and computing infrastructures, and then taking advantage of poor cybersecurity to steal medical health records, deny access to health services, or cause intentional harm with these.[10][11] For medical devices specifically, it may be possible for hackers to use them in order to gain access to confidential patient data and to reprogram them to send harmful commands.[12] This could mean, for example, altering blood groups or test results, or taking control of pumps that regulate the administration of potent drugs.[13] Other harmful activities that could be enacted include disrupting the parameter values used in the scanning protocols, tampering with the radiation exposure levels, causing mechanical disruption, and creating denial-of-service attacks.[14]
Other researchers have also investigated the subject of cybersecurity in medical devices and have concluded that there is a relationship between the increase in network connectable medical devices and increased cybersecurity risks.[15] As such, segmenting the network into multiple layers, with security gates such as firewalls in between them, could be an effective way to contain network problems and reduce the impact of a breach in network security.[16][17] This is comparable to dividing a building into fire zones to delay fire spreading, and enabling firefighting in sections rather than in the building as a whole.[18]
Applying the concept of network segmentation to medical devices may reduce the associated risks and prevent intrusion. This entails separating elements such as computers, servers, routers, data, and healthcare personnel into groups, thereby restricting access and better protecting vital services.[19][20] Segmentation of medical devices is described as a good method for ensuring data security and is recommended to be used to whatever extent is feasible.[21] In order to increase understanding of innovations in healthcare organizations, such as segmentation of medical devices, Länsisalmi et al.[22] argue that health innovations should be investigated from the perspectives of stakeholders, in this case IT and MT personnel. Therefore, the aim of this study was to investigate IT and MT personnel’s perception of segmentation of medical devices and IT infrastructure in the healthcare sector.
Highlights of this study:
- Medical devices can cause substantial harm.
- The user of medical devices must understand how to achieve a high level of security.
- Hackers might be able to reprogram medical devices to send harmful commands.
- One way to reduce the risk of hackers and prevent intrusion is network segmentation.
- MT and IT personnel must be positive about and open to the improvement of cybersecurity.
Materials and methods
Design and setting
A qualitative methodology design was employed with focus group sessions in order to gain a deeper insight into the views and experiences of IT segmentation. This descriptive study was conducted at Region Skåne, one of the 21 county councils/regions in Sweden. Region Skåne employs around 34,000 people, mostly in healthcare, and has the main responsibility for public healthcare and medical services in the region.[23] Much of the healthcare is conducted in a high-tech environment, which includes devices such as patient monitoring equipment, medical imaging systems, and laboratory instrumentation. A number of cybersecurity-related incidents prompted a decision to implement network segmentation for all devices in Region Skåne. The study was performed during the ongoing implementation of the network segmentation of medical devices.
Informants
Informants were strategically recruited from IT and MT personnel based on their experience working with medical devices such as patient monitoring equipment, medical imaging systems, and laboratory instrumentation in Region Skåne to ensure maximal variation in socio-demographic data and service positions.[24] The following variables were taken into account to ensure a broad selection: age, time in the profession, and competence in (1) segmentation, (2) MT device systems, (3) firewall-based traffic filtering, and (4) IT security.
Ethics
The study conformed to the principles outlined in the Declaration of Helsinki, and according to Swedish legislation (SFS 2003:460) no ethical approval was required as the study did not involve patients. The project was approved by the directors of the participating departments. All informants were informed of the aims and procedures of the study through a short written presentation included in an email invitation. Informed consent was considered implied when informants signed up voluntarily for the focus group interviews. The data processing was carried out in accordance to the General Data Protection Regulation (GDPR).
Data collection
Three mixed MT and IT focus group interviews[25] were held with five to eight informants in each group and included a total of 18 informants (nine MT personnel and nine IT personnel; see Table 1 for demographic and other characteristics). Interviews were conducted in a conference room and took about 90 minutes each. The discussions were digitally recorded (with the informants’ consent) and independently transcribed by a trusted agency.
| ||||||||||||||||||||||||||
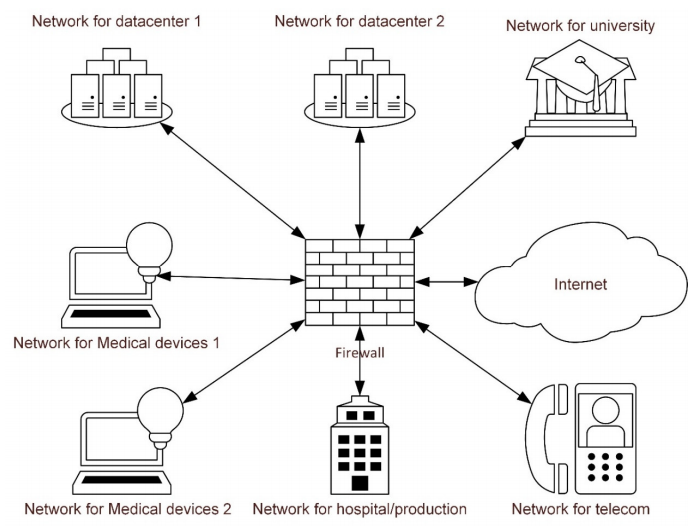
The interviews were conducted with one researcher who had extensive experience in focus group interviews acting as moderator and a second acting as assistant. A short presentation of network segmentation was held prior to discussions as an introduction to the topic. A rough outline of network segmentation and specifically how it relates to the segmentation of medical devices was also presented (see Figure 1). The interviews focused on positive expectations and misgivings about the solution. Informants were asked two open-ended questions: “What are the advantages of segmentation of medical devices?” and “What misgivings do you have regarding segmentation of medical devices?” Probing questions were also used.
|
Data analysis
The text from the interviews was analyzed using qualitative content analysis.[26][27] Transcribed interviews were first read as a whole by all authors to gain an overall understanding. The text was then divided into meaningful units, which were condensed, coded, and gathered into groups with similar content. These steps were carried out by the authors individually, and then all authors gathered and discussed the findings. These were then abstracted into subcategories that met the study aim. Finally, the subcategories were abstracted into two categories. An example of the analysis process can be found in Table 2. The statements were thoroughly assessed by the authors to ensure that no statements relating to positive expectations or misgivings regarding segmentation were left out due to the condensation of meaning units into codes.
| ||||||||||||||||||||
Results
Two categories emerged during the analysis of the transcribed interviews: “Information security” and “Implementation of segmentation in healthcare.” These categories contained six subcategories (Table 3).
| ||||||||
Information security
Outsider threats
Across the three focus groups, attacks originating from outside of the healthcare organization were well known, and the informants had personal experience of such attacks or had heard of them from others. Virus attacks that led to numerous problems and increased work had been experienced. Informants were, on the whole, positive to the possibilities of limiting data virus infections that are offered by segmentation technology, as well as the potential increase in patient safety. They were also positive to the increased protection that segmentation offered to older applications unable to withstand outsider threats due to patching policies or lack of security design.
It was stated that segmentation reduces the risk that core systems or patients will be affected during an infection of malicious software or hacker attacks/intrusions, primarily by restricting access between technical devices.
As Informant 3 put it: “The thing is, that you can divide up and protect … When you look at virus attacks and other things, that it doesn’t affect different segments but stays within the same segment … That’s the advantage as I see it.”
Insider threats
In relation to insider threats, informants had experienced personnel accidentally forwarding infected emails, which caused great harm. They perceived that segmentation would reduce the risk of users getting hold of restricted information via administrative interfaces that they should not have access to, thereby reducing the probability of them making administrative mistakes. It also would reduce the probability that users, whether by mistake or intention, introduced malicious code into medical devices and/or core infrastructure. The informants opined that with segmentation, devices would be less likely to be incorrectly configured when connected to the network, thereby reducing the likelihood of failures or connection issues and, in turn, improving patient security. Informant 2 adds: “… It doesn’t have to be malicious, of course, you might make a mistake just because you have access to things that you shouldn’t have.”
However, the informants expressed the benefits of segmentation would be cancelled out, however, due to the risk that so many openings would be needed between segments due to the large number of older devices.
Implementation of segmentation in healthcare
Predictions of an increase in costs and administration
The informants, in general, predicted an increase in administration and costs for the organization. Because of the higher level of complexity introduced by segmentation, the informants predicted that working with a segmented network would require better planning and documentation. A positive side effect of this would be a better understanding of future costs for the healthcare organization, which would be especially useful for detecting increased costs due to deviating or nonstandard network communication solutions for medical technology. It was also expected that segmentation would lead to better planned maintenance work for medical technology solutions since network communication would be more controlled and structured.
The informants assumed that implementing segmentation would increase administrative tasks and the need for resources (i.e., make it time consuming) due to the increased number of firewalls between segments, and openings needed in these. Also, new processes, routines, and administrative tools would be needed, such as automated software. There were, therefore, misgivings that segmentation would lead to longer execution times and that increased planning would be required for network changes.
Informant 17 puts it as such: “I see it [implementation] as very resource-intensive to implement … [with] longer lead times and complicated administration.”
Predictions of required knowledge improvement for the healthcare organization
The informants perceived that their own knowledge and competence regarding network communication would need to improve, due to a higher level of complexity. Informants had positive expectations of receiving the necessary education and assumed that management felt the same way. However, the informants also stated the importance of informing all relevant parties about the strategy and goal of the network segmentation, including, for example, personnel affiliated with system management and medical technology devices within the healthcare organization.
Informant 1 states: “I see an advantage and a disadvantage in the fact that more knowledge is required … not only from us, but also from our suppliers … With segmentation, we will need a better understanding of all of our systems.”
Possibilities and pitfalls concerning segmentation
The informants perceived that the segmentation solution provided an opportunity to use the infrastructure to provide restricted communication rights based on actual needs of users and systems, which would provide a high degree of flexibility and thereby better preparedness for new communication requirements. It also presented an easier way to reuse the infrastructure. They also expressed that the design gave an advantage by isolating attacks through the network in an easier way, and that it gave the basis for a more controlled and secure network operations environment by reducing the impact of changes and faults between network segments. Furthermore, they said that dedicated network segments for remote administration would give fewer attack vectors between systems.
The informants highlighted the need to communicate overall policies and designs, as well as guidelines for implementation of segmentation, to avoid counterproductive effects. One such effect could be creating too many openings between the segments so that the key benefits of segmentation would be lost.
Per Informant 18: “Segmentation is really about trying to minimize consequences … If we discover that one segment has a virus … then we shut down the framework, which means that it’s completely isolated.”
Increased demands on medical device manufacturers
The informants had also experienced working with medical device manufacturers who connect to medical devices remotely. It was foreseen that requirements for knowledge, planning ability, and documentation from manufacturers of how their devices work and how they integrate with other devices would increase once segmentation was completed. This would give increased insight into devices, something that informants perceived as currently lacking, both in customers and manufacturers. However, this could also lead to increased cost. “… And then I think another problem could be that our suppliers, they don’t always know exactly how their applications talk to each other, which ports are used. So that could also be challenging to get right,” adds Informant 15.
Segmentation was also expected to give an opportunity for manufacturers to connect to devices for support in more diverse and secure ways. For instance, it would be possible to allow forms of communication other than virtual private network (VPN) without affecting the overall security level. It would also be possible to reduce manufacturer’s access rights to other systems, thus reducing the risk of manufacturer-induced faults (paraphrasing of comments from Informant 5).
Discussion
This qualitative study provides insights into the perceptions among IT and MT personnel after a decision to implement network segmentation of medical devices and IT infrastructure in the healthcare sector. Despite the fact that this is a small study, the results corroborated that healthcare systems are complex structures, and medical devices that are integrated into a hospital’s IT systems are just a minor part of the system as a whole. However, these devices play a critical role in clinical function. If a medical device fails, there are many potential hazards to patient safety. There are many techniques for increasing cybersecurity, including not only network segmentation but also security policies, antivirus software, lifecycle management of operating systems, security patches, drivers, and so on.[15] Hopefully, the present study may partly provide support and inspire healthcare organizations to develop and communicate a strategy that encompasses all these important parts. Generally, security can be further enhanced if the segmentation is implemented with rigorous and strictly enforced security controls regarding communication between segments. As such, the communication boundaries between segments will not stop cyberattacks entirely unless the network also complies with rules, standards, and requirements that emphasize access control policies using a so called “next-generation firewall” (NGFW) implementation, which includes additional network device-filtering functionalities such as an intrusion prevention system (IPS), intrusion detection protocol (IDP), activity logging, and web and mail security features. A simple application layer firewall cannot stop camouflaged malware from causing security risks to healthcare facilities.
In this study, which focused specifically on expectations and misgivings regarding segmentation, there were two themes that emerged across the categories identified in the analysis, namely information security and implementation of segmentation in healthcare. The informants in the study had experience of insider and outsider threats. In May 2017, a major ransomware attack called WannaCry occurred, which affected 200,000 systems in around 150 countries worldwide.[13] In the U.K., 50 hospitals were affected, patient safety was threatened, and there were calls to highlight cybersecurity in healthcare.[13] In the present study, informants assumed that insider and outsider threats and threats from malicious software, such as ransomware, would decrease with the use of segmentation. Besides the advantages pointed out by the informants, segmentation adds additional security measures to hinder attack vectors. An example is the possibility to deny certain types of network traffic on layer seven of the Open Systems Interconnection (OSI)-stack (i.e., message handling in the application layer), which allows detection of communication patterns. This will decrease the spread of malicious code and denial-of-services threats. Medical devices are regarded to have a low capability of defending themselves against these sorts of threats and will benefit greatly from the added security layers. It could be speculated that if all England's hospitals had implemented segmentation of medical equipment ahead of the WannaCry attack[13], the impact would probably have been lessened as the dispersion could have been limited. If this were the case, hospitals could have continued to produce care and thus maintained a higher level of patient safety, especially if there had been support for technologies such as an intrusion prevention system (IPS). However, healthcare organizations need to be aware that segmentation, although important, is just one measure to increase cybersecurity; relying on it solely could give a false sense of security.
Informants in the study opined that with segmentation, the demand for documentation would increase regarding communication between infrastructure components within and between systems. It was also opined that the number of firewall changes (i.e., allowed network traffic patterns between segments) and the overall workload of the network and system administrators would increase, which, in turn, would lead to technical skills and increased costs. These opinions are important to take into account from a change management perspective as the informants represent a critical success factor in achieving a high cybersecurity level. Under-investing in cybersecurity is not unique for Sweden. It has previously been pointed out that compared to other sectors that spend four to ten percent of their budget, the healthcare sector spends a relatively small amount (one to two percent) of its budget on IT infrastructure. This must be reconsidered so that fundamental patient safety, healthcare technology, and functionality are not compromised.[13][28] It can be stated that, as healthcare organizations are relying more and more on digital technologies, both regarding medical and other systems, the need for cybersecurity will also become more aligned with other sectors, such as industries and banks.
On the basis of the present study, the suggestion of a more structured way of working can be perceived as less flexible with regard to changes, from an administrative point of view, while requiring new processes and new supporting software. On the positive side, segmentation will give better insight into the communication landscape, and a better overview. Historically, cyberattacks have had a significant impact on production, generating high costs for the targeted organization; the healthcare sector must find cost-effective ways to prevent such potentially devastating costs.[13] It must also be assumed that the confidence of stakeholders (patients, manufacturers, and institutions) in the healthcare organization will be reduced after a successful cyberattack.
Our results showed a need for improvement in the level of competence, as the informants assumed that a greater knowledge base would be required due to the higher level of complexity associated with segmentation. This corroborates a Swedish study showing that a majority of IT and MT personnel considered recurrent training on IT and MT safety, rules, and regulations, as well as a risk analysis with a focus on patient safety, to be of great importance.[7] It is also important that the goals and importance of segmentation are communicated throughout the organization, and the processes and guidelines established regarding system placement within the different segments. The healthcare organization must commit to and supply the means for education and training.
The informants in this study assumed that segmentation would provide more efficient and flexible ways of working for healthcare personnel since changing network sockets will not result in additional administrative tasks. Also, dedicated segments for remote administration add better control and logging capabilities in relation to external users, such as medical device suppliers providing support. The informants also identified a great need for thorough planning before the implementation of segmentation, to make the administration, configuration, and traffic analysis manageable for the organization. The number of segments increases the amount of hardware required, and it is also important to plan where medical devices are placed to minimize administration between segments.
In order to meet the needs of cybersecurity of the future, the present study stated that the knowledge level of medical device manufacturers, in general, needed to be increased in association with segmentation. It has earlier been highlighted that increased collaboration between medical device manufacturers and personnel in the healthcare sector is fundamental to ensure effective protection.[29] One effect of segmentation is that suppliers will gain new possibilities to connect to their medical devices within the healthcare organization, for example, during support cases. Segmentation will not reduce the regulation and security requirements that suppliers need to commit to. This is in agreement with[30] that stated the manufactures had challenges to meet regulation and safety standards including lifecycle management to improve medical device cybersecurity. It is, therefore, important that requirements regarding connection for remote maintenance and support are clearly agreed to during the acquisition process for new medical devices.
We believe mixed IT/MT focus groups increased coverage of the subject area and provided openness in discussions regarding to being better able to extract novel insights and various expert knowledge. However, because of the study’s qualitative nature, the aim was not to generalize the results to the healthcare sector as a whole. However, it is reasonable to assume that the results show a part of the reality of healthcare in one county council as well as give a better understanding of cybersecurity issues. A review on cybersecurity stated that there are very few studies in the area which include human and organizational aspects, as well as strategy and management. This may justify the present study.[31] A question we have asked ourselves is whether the outcome would have been different if the interviews had been held in the near future after an attack like the WannaCry ransomware attack.[13] That attack is one more indication that cybersecurity policies must be in place for proactive use in the healthcare section and widely communicated, even if the cost seems high. Further, a large (country-scale) study of the implementation of network segmentation would be of interest for further research, and also a study of the health economic impact of a cyberattack.
Conclusion
Network segmentation decreases the probability of spreading malicious software and intrusions through a network by introducing barriers between network areas, much in the same way fire zones decreases the probability for fire spreading in a building. Medical devices have historically not had a focus on security features. In this study, it was apparent that MT and IT personnel were positively receptive to the increase in cybersecurity provided by network segmentation but concerned about the increase in the administration that it will entail for medical devices. These opinions are important to take into account to be able to reach the desired increase in cybersecurity. Cybersecurity risks are multifaceted. The present study can be used as a model for other clinical healthcare manufacturers to increase awareness of concerns and opinions in personnel and healthcare organizations in general.
Acknowledgements
We are grateful to the informants who took part in this research and would also like to thank the Medical Services, Region Skåne, Sweden, for their support.
Author contributions
Conceptualization, B.I. and D.J.; methodology, B.I. and M.C.; formal analysis, D.J., B.I., P.J. and M.C.; investigation, B.I. and M.C.; writing—original draft preparation, B.I., D.J. and M.C.; writing— review and editing, D.J., B.I., P.J. and M.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflict of interest
The authors declare no conflict of interest.
References
- ↑ European Commission (14 June 1993). "Council Directive 93/42/EEC of 14 June 1993 concerning medical devices". EUR-Lex. https://eur-lex.europa.eu/eli/dir/1993/42/2007-10-11. Retrieved 20 January 2020.
- ↑ Abernethy, A.P.; Wheeler, J.L.; Bull, J. (2011). "Development of a health information technology-based data system in community-based hospice and palliative care". American Journal of Preventative Medicine 40 (5 Suppl. 2): S217–24. doi:10.1016/j.amepre.2011.01.012. PMID 21521597.
- ↑ McCaffery, F.; Burton, J.; Richardson, I. (2010). "Risk management capability model for the development of medical device software". Software Quality Journal 18: 18. doi:10.1007/s11219-009-9086-7.
- ↑ Tulasidas, S.; Mackay, R.; Craw, P. et al. (2013). "Process of Designing Robust, Dependable, Safe and Secure Software for Medical Devices: Point of Care Testing Device as a Case Study". Journal of Software Engineering and Applications 6 (9A): 1–13. doi:10.4236/jsea.2013.69A001.
- ↑ Arney, D.; Venkatasubramanian, K.K.; Sokolsky, O.; Lee, I. (2011). "Biomedical devices and systems security". Conference Proceedings of the IEEE Engineering in Medicine and Biology Society 2011: 2376-9. doi:10.1109/IEMBS.2011.6090663. PMID 22254819.
- ↑ Jha, A.K.; Prasopa-Plaizier, N.; Larizgoitia, I. et al. (2010). "Patient safety research: an overview of the global evidence". Quality and Safety in Health Care 19 (1): 42–7. doi:10.1136/qshc.2008.029165. PMID 20172882.
- ↑ 7.0 7.1 Ivarsson, B.; Wiinberg, S.; Svensson, M. et al. (2016). "Information and/or medical technology staff experience with regulations for medical information systems and medical devices". Health Policy and Technology 5 (4): 383–88. doi:10.1016/j.hlpt.2016.07.008.
- ↑ Nurse, J.R.C.; Buckley, O.; Legg, P.A. et al. (2014). "Understanding Insider Threat: A Framework for Characterising Attacks". 2014 IEEE Security and Privacy Workshops: 214-228. doi:10.1109/SPW.2014.38.
- ↑ de Brujin, H.; Janssen, M. (2017). "Building Cybersecurity Awareness: The need for evidence-based framing strategies". Government Information Quarterly 34 (1): 1–7. doi:10.1016/j.giq.2017.02.007.
- ↑ Fischbacher-Smith, D.; Fischbacher-Smith, M. (2013). "The Vulnerability of Public Spaces: Challenges for UK hospitals under the ‘new’ terrorist threat". Public Management Review 15 (3): 330–43. doi:10.1080/14719037.2013.769851.
- ↑ Coventry, L.; Branley, D. et al. (2018). "Cybersecurity in healthcare: A narrative review of trends, threats and ways forward". Maturitas 113: 48–52. doi:10.1016/j.maturitas.2018.04.008. PMID 29903648.
- ↑ Leavitt, N. (2010). "Researchers Fight to Keep Implanted Medical Devices Safe from Hackers". Computer 43 (8): 11–14. doi:10.1109/MC.2010.237.
- ↑ 13.0 13.1 13.2 13.3 13.4 13.5 13.6 Martin, G.; Martin, P.; Hankin, C. et al. (2017). "Cybersecurity and healthcare: How safe are we?". BMJ 358: j3179. doi:10.1136/bmj.j3179.
- ↑ Mahler, T.; Nissim, N.; Shalom, E. et al.. "Know Your Enemy: Characteristics of Cyber-Attacks on Medical Imaging Devices". arXiv. https://arxiv.org/abs/1801.05583.
- ↑ 15.0 15.1 Schwartz, S.; Ross, A.; Carmody, S. et al. (2018). "The Evolving State of Medical Device Cybersecurity". Biomedical Instrumentation and Technology 52 (2): 103-111. doi:10.2345/0899-8205-52.2.103. PMID 29558182.
- ↑ Reichenberg, N. (20 March 2014). "Improving Security via Proper Network Segmentation". Security Week. https://www.securityweek.com/improving-security-proper-network-segmentation. Retrieved 20 January 2020.
- ↑ Hagland, M. (26 February 2018). "A New Era in Network Segmentation?". Healthcare Innovation. https://www.hcinnovationgroup.com/cybersecurity/article/13029865/a-new-era-in-network-segmentation. Retrieved 20 January 2020.
- ↑ Hiemstra, H. (2016). "Influence of Building Structure and Building Content on Residential Fires". Master's Thesis. Lund University. https://lup.lub.lu.se/student-papers/search/publication/8876361.
- ↑ Genge, B.; Graur, F.; Haller, P. (2015). "Experimental assessment of network design approaches for protecting industrial control systems". International Journal of Critical Infrastructure Protection 11: 24–38. doi:10.1016/j.ijcip.2015.07.005.
- ↑ Sitting, D.F.; Singh, H. (2016). "A Socio-Technical Approach to Preventing, Mitigating, and Recovering from Ransomware Attacks". Applied Clinical Informatics 7 (2): 624–32. doi:10.4338/ACI-2016-04-SOA-0064. PMC PMC4941865. PMID 27437066. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC4941865.
- ↑ Todinov, M. (2015). "Reducing Risk through Segmentation, Permutations, Time and Space Exposure, Inverse States, and Separation". International Journal of Risk and Contingency Management 4 (3): 1–21. doi:10.4018/IJRCM.2015070101.
- ↑ SLänsisalmi, H.; Kivimäki, M.; Aalto, P.; Ruoranen, R. (2006). "Innovation in healthcare: A systematic review of recent research". Nursing Science Quarterly 19 (1): 66–72. doi:10.1177/0894318405284129. PMID 16407603.
- ↑ Anell, A.; Glenngård, A.H.; Merkur, S. (2012). "Sweden health system review". Health Systems in Transition 14 (5): 1–159. PMID 22894859.
- ↑ Fridlund, B. (1998). "Qualitative methods in healthcare research: Some issues related to utilisation and scrutiny". Care of the Critically Ill 14 (6): 212–14. http://urn.kb.se/resolve?urn=urn:nbn:se:hj:diva-12022.
- ↑ Bowling, A. (2014). Research Methods in Health: Investigating Health and Health Services (4th ed.). Open University Press. ISBN 9780335262748.
- ↑ Graneheim, U.H.; Lundman, B. (2004). "Qualitative content analysis in nursing research: concepts, procedures and measures to achieve trustworthiness". Nursing Education Today 24 (2): 105–12. doi:10.1016/j.nedt.2003.10.001. PMID 14769454.
- ↑ Burnard, P. (1996). "Teaching the analysis of textual data: An experiential approach". Nursing Education Today 16 (4): 278–81. doi:10.1016/s0260-6917(96)80115-8. PMID 8936234.
- ↑ Kruse, C.S.; Frederick, B.; Jacobson, T.; Monticore, D.K. (2017). "Cybersecurity in healthcare: A systematic review of modern threats and trends". Technology and Health Care 25 (1): 1–10. doi:10.3233/THC-161263. PMID 27689562.
- ↑ Webb, T.; Dayal, S. (2017). "Building the wall: Addressing cybersecurity risks in medical devices in the U.S.A. and Australia". Computer Law & Security Review 33 (4): 559–563. doi:10.1016/j.clsr.2017.05.004.
- ↑ Regan, G.; McCaffery, F.; McDaid, K. et al. (2013). "Medical device standards' requirements for traceability during the software development lifecycle and implementation of a traceability assessment model". Computer Standards & Interfaces 36 (1): 3–9. doi:10.1016/j.csi.2013.07.012.
- ↑ Jalali, M.S.; Razak, S.; Gordon, W. et al. (2019). "Health Care and Cybersecurity: Bibliometric Analysis of the Literature". Journal of Medical Internet Research 21 (2): e12644. doi:10.2196/12644. PMC PMC6396074. PMID 30767908. https://www.ncbi.nlm.nih.gov/pmc/articles/PMC6396074.
Notes
This presentation is faithful to the original, with only a few minor changes to presentation, grammar, and punctuation. In some cases important information was missing from the references, and that information was added.